Protecting Your Business Against Social Engineering and Cyber Threats
The cost of cyber attacks is rising for small and medium businesses (SMBs). A Kaspersky Lab 2017 survey found that cyber breaches can cost small and medium businesses $177K per incident. In the past, only large corporations had to worry about cyber attacks. Cybercriminals were mainly interested in penetrating the security systems of corporations. However, as small and medium businesses started to get involved in online financial dealings, cybercriminals realized that these organizations were valuable targets. Additionally, SMBs don’t have the enormous resources of enterprises. So they are more vulnerable.
A Personal Example with a Client
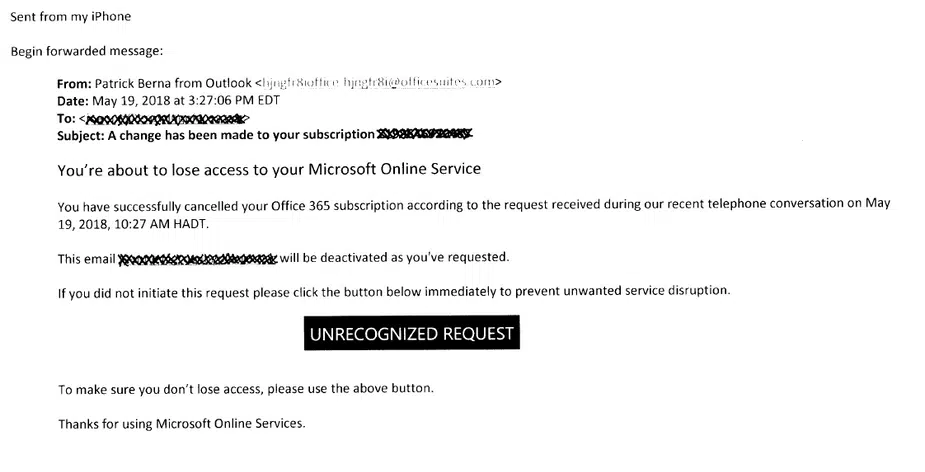
At Cleartech Group, we help our clients with their Microsoft Office 365 setup and security. A few days ago, one of our best clients forwarded the following email to us:
The client wanted to find out if the email was legitimate. It was obvious to us that it was a phishing scam. We advised her to delete the email immediately. We also told her not to click on any links or attachments.
Our client’s decision to reach out to us was the right decision. We were glad to help her prevent a catastrophe. If something doesn’t feel right, you should always get a second opinion. It helps to have trusted advisers on your side. In the internet age, a few clicks can expose your business to severe security risks.
Most people think that cyber attacks are conducted by genius hackers. You’ll be surprised to learn that most attacks use simple social engineering techniques. “Social engineering” is a fancy term for psychological manipulation.
The social engineering techniques used in cyber attacks have been around for centuries. They just got a makeover in the digital age. Awareness and knowledge can help you prevent these attacks. So it’s a good idea to learn about the common techniques.
Commonly Used Social Engineering Techniques
Social engineering techniques exploit human trust. Here are a few popular ones:
Phishing: Phishing scams are the most popular as they are easy to orchestrate. You’ll receive a communication that will tell you that you need to contact them immediately. The end goal is to get personal information like social security, financial information, account passwords, and other sensitive data.
Baiting: Baiting is a cousin of phishing. Instead of using urgency, baiting takes a more patient approach. Baiting communications use valuable rewards, like cash prizes or expensive products, as lures. These attacks are also called Quid Pro Quo because the attackers promise to give you something in return for something from you.
Whaling: Whaling is also a form of phishing attack. But the targets are big fishes or whales like the C-level executives. The communications for these attacks are more sophisticated than general phishing attacks. It’s often used for corporate espionage.
Malvertising: This is also known as malicious advertising. Cybercriminals attach malicious code to advertisements. Avoid unreliable sites to prevent this type of attack. Unfortunately, even valid sites can have malvertising. Always be cautious about clicking on ads.
Pretexting: In this technique, the attackers use storytelling and pretending to be someone else to gain the trust of the target. For example, they can call you as a representative of a power or cable company and ask for your password. Whenever you receive an unexpected call, make sure you can properly verify the caller’s identity.
Piggybacking: In most cases, cyber attacks are digital. However, hackers often use old-school methods and get access to computer resources by entering restricted areas. Piggybacking, also known as tailgating, is a technique where the cybercriminal waits near an entry-point or door and enters the restricted area by just following an employee who is entering the area. The attackers rely on the fact that the employee might not ask for identification due to common courtesy.
In Conclusion
Vigilance is an important part of securing your infrastructure. Education of your employees can eliminate vulnerabilities. Also, trusted advisers can help you with your security weaknesses. Awareness, caution, and the right expertise can go a long way to prevent future breaches.
Are you confident about your protection against social engineering attacks? At Cleartech Group, we have built a team with great cybersecurity and IT experience. As a trusted adviser, we can help you find your vulnerabilities and secure your network. Contact us today at (978) 466-1938 or reach out online. Our experts are ready to help.